Integration Checklist
Follow our guidelines for building a secure and resilient application.
This guide provides a step-by-step checklist to connect your systems with Fortis APIs. You will learn how to request access, configure your environment with mTLS, and make your first successful API call to verify your setup.
The onboarding process involves three key phases: you submit a request, our team provisions your credentials, and you verify the connection.
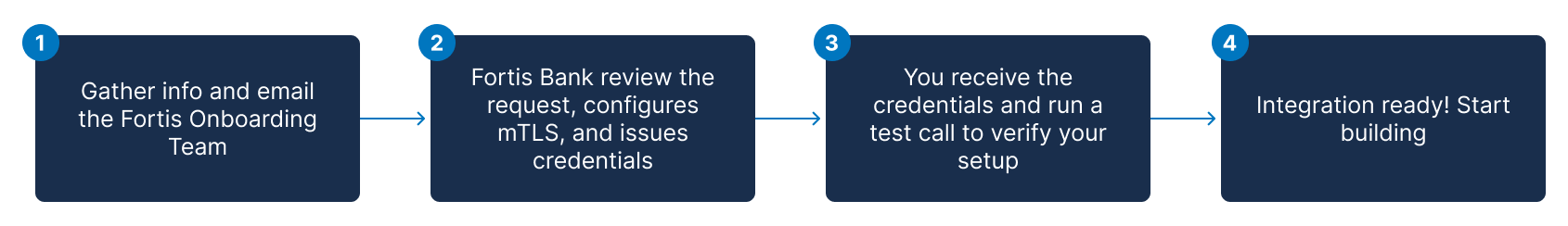
To begin, contact our team trough the Contact Us form.
Please include the following information in your message:
Please allow 1-2 business days for our team to process your request and provision your credentials.
Once your request is approved and your certificate is configured, the Fortis team will securely provide your unique OAuth 2.0 credentials:
client_idclient_secretStore these credentials in a secure location, such as a managed secrets vault. You will use them in the next step to generate a bearer token for your API calls.
You will receive Sandbox environment credentials, for further environments please contact the Fortis Bank team.
XSignatureTo ensure the integrity and authenticity of the webhook payload you receive, you must validate the provided XSignature against the data. To understand how Fortis creates the XSignature, see the steps below:
First we combine the following four values in a specific order to form a single string:
POST).https://webhooks.test.com/v1/webhooks).1757427083).Using the example values provided, the resulting concatenated string is:
POSThttps://webhooks.test.com/v1/webhooks{"notificationId":"73a3ee45-8d56-4be6-9307-7456e92d0b75","eventType":"gen.trans.info","eventDateTime":"2025-09-02T17:24:50.000-06:00","data":{"generalTransactionEventInfo":{"accountId":"123456789","accountType":"D","amount":"10.00","type":"Cr","description":"Misc Credit","category":"","channel":null,"classification":null,"receiptId":"XXX1234567","exceptionInfo":[]}}}1757427083
We use the HMAC-SHA256 algorithm to create a hash of the concatenated string. The hash is generated using your HMAC Secret Key as the key.
The general formula is: HMAC-SHA256(secretKey, concatenatedString).
HMAC-SHA256("123ANO8uA9qkmBnWA4LqfcffgEOZKLlOQQcPkLOO4XU=", "POSThttps://webhooks.test.com/v1/webhooks...")
Lastly, we encode the raw HMAC output into a hexadecimal string. The resulting hexadecimal string is the final signature.
For the given example, the final XSignature is:
4bbe332610334c124999141a335a2a354bd098b3464023701062cf963390e494
Use this sample as a way to guide you in deconstructing the XSignature to perform validations.
Before integrating with any environments endpoints, verify that your credentials and mTLS setup are working correctly. You can do this by calling the simple and secure Hello Fortis API available across all environments.
This single test confirms your entire setup:
client_id and client_secret can be used to generate a valid access token.First, use your credentials to get a bearer token from our OAuth 2.0 API. The response will contain your access_token. After, use that token to call the Hello Fortis API.
A successful 200 OK response with a confirmation message means your setup is correct and you are ready to start building. If you receive an error, check the Error Codes page for troubleshooting guidance.
With your connection verified, you are ready to integrate. We recommend reviewing the following documentation to ensure a robust and secure implementation.